HIPAA Compliance for the US market
Requirements defined by HIPAA and HITECH

What is HIPAA
HIPAA (Health Insurance Portability and Accountability Act) is an American legislation aimed at improving the efficiency and effectiveness of the health care system in the US. Every business processing electronic Protected Health Information (ePHI) within the US needs to comply with it. It is administered under the HHS (Department of Health & Human Services).HIPAA is composed of 4 main parts. They are:
- Privacy Rule
- Breach Notification Rule
- Enforcement Rule
- Security Rule
The requirements relating to security are contained in the eponymoous Security Rule, which “establish[es] a national set of security standards for protecting certain health information that is held or transferred in electronic form.”
Who is covered by the security Rule
Covered Entities
The Security Rule applies to what the HIPAA defines “covered entities”, namely: “health plans, health care clearinghouses, and to any health care provider who transmits health information in electronic form in connection with a transaction for which the Secretary of HHS has adopted standards under HIPAA.”
Business Associates
As a result of the HITECH Act of 2009, HIPAA has been extended to cover "Business Associates" as well. These are “a person or entity that performs certain functions or activities that involve the use or disclosure of protected health information on behalf of, or provides services to, a covered entity.” As a digital health business you can act on behalf of a Covered Entity or directly collect ePHI from an individual.
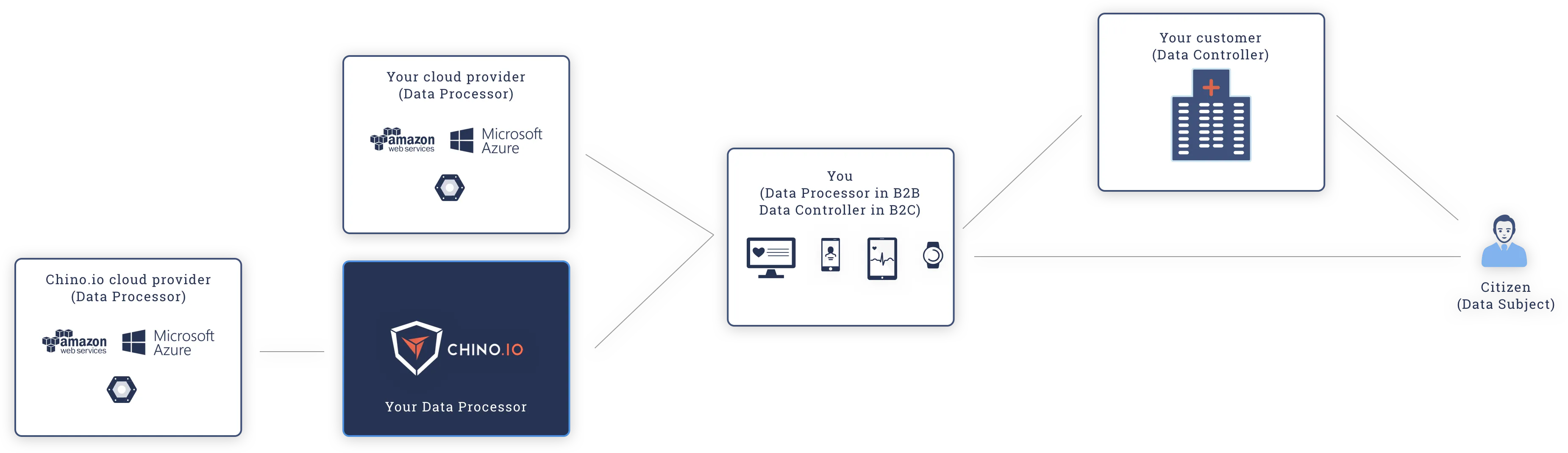
How Chino.io can help
Implementing the requirements of the Security Rule is complex, expensive, risky and time-consuming. Chino.io strengthens all safeguards, offering developers a set of APIs that can be easily integrated within apps or servers to store sensitive data securely.
